Product Specs
| Created by | Dheeraj CSE |
|---|---|
| File type | RAR, ZIP |
| File size | 32.80 KB |
| Date of Creation | March 30 2025 |
| Color | black blue red yellow |
| Rating | 5 (10) |
| Category |
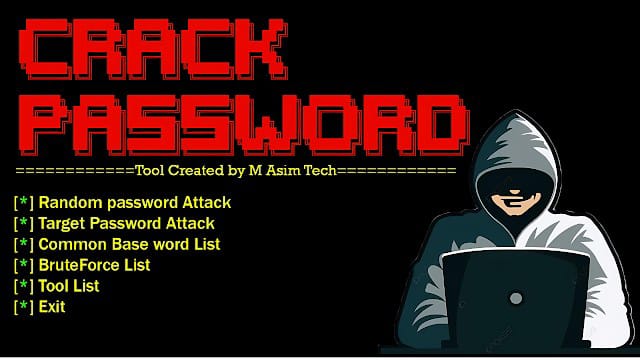
1.Random Password Attack
2.Traget PASSWORD Attack
3.Common Base Wprd List
4.Brute -Forcce Attack
5.Tool List
Random Password Attack – This attack generates random passwords without any pattern, attempting multiple combinations until access is gained.
Target Password Attack – Focuses on a specific user by trying passwords related to their personal details, such as names, birthdays, or common phrases they use.
Common Base Word List – Uses precompiled lists of frequently used passwords (e.g., “123456”, “password”) to guess login credentials efficiently.
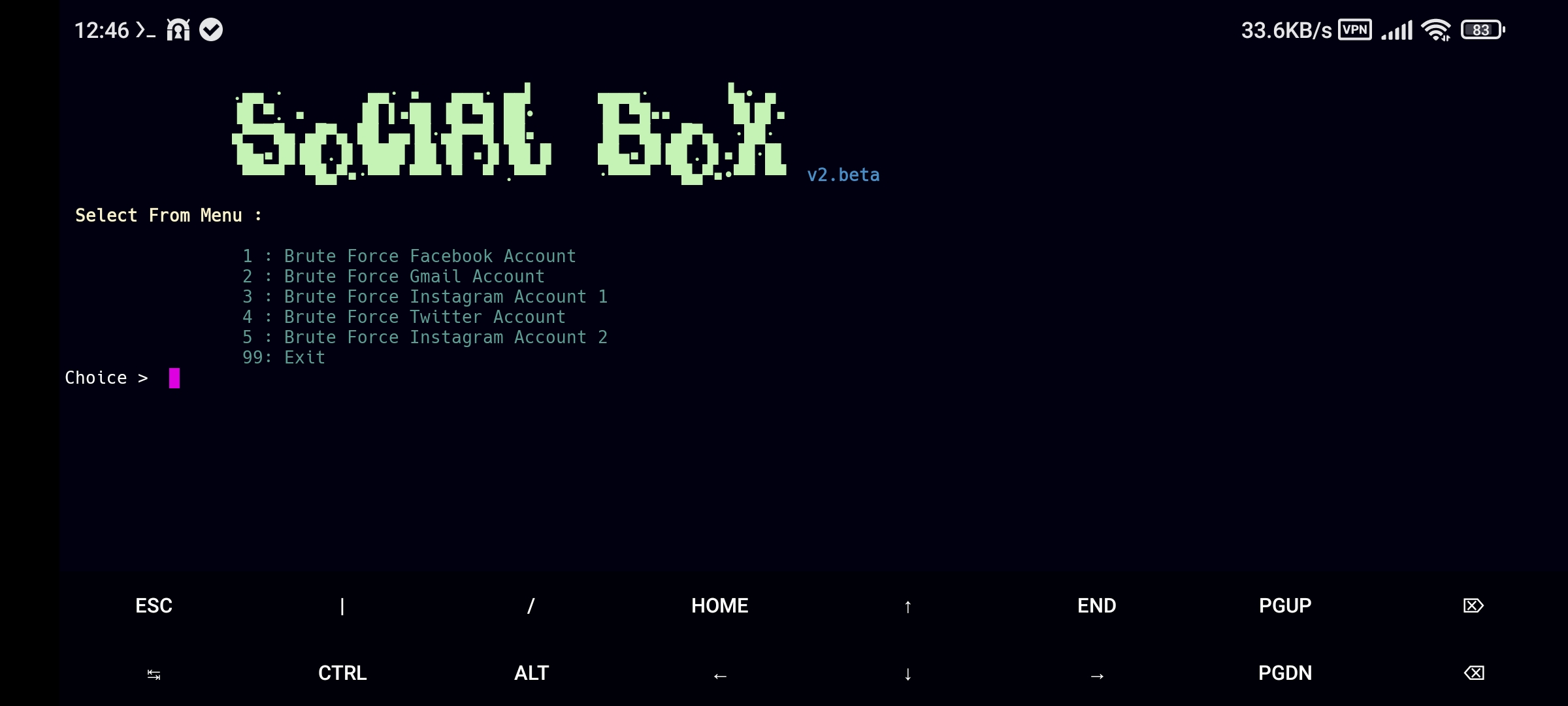
Brute-Force Attack – Systematically tries all possible password combinations until the correct one is found, often using automated tools for speed.
Tool List – Popular tools include Hydra, John the Ripper, Aircrack-ng, Hashcat, Medusa, and THC Hydra, used for password cracking and security testing.